Password security is a crucial aspect of every WordPress website. A weak pass, or a compromised one, can grant attackers full access to the admin dashboard, database, personal data, and even the server your website is uploaded on.
For quite some time, MD5 was the standard for hashing passwords, but today it is considered insecure and obsolete. Nowadays, WordPress adopts contemporary and more trustworthy algorithms such as bcrypt, but such protection is of no use should the website be poorly designed and use old plugins and other legacy software.
In this article, we share why MD5 is not trustworthy and share some tips on how to prevent WordPress MD5 hash decrypt exploits, to make your WordPress more secure and reliable.
What is MD5 Hash
MD5 is a system that hides your password behind a string of random symbols. For example, if your password is “abc123”, via MD5 it is masked like 0192023a7bbd73250516f069df18b500. This approach is designed to help you keep your password safe, and when working with databases, still see a hashed version of the pass, so no one steals it right away.
However, MD5 is already an old and obsolete technology that can be easily hacked. This is why contemporary developers have turned to other password protection methods and have slowly and completely abandoned MD5.
Read also: How to Change WordPress Password
Does WordPress Still Use MD5 Hash
New versions of WordPress no longer adopt MD5 hash, and instead they rely on PHP protection that is considered way better than the old-school hashing method.
However, there’s a chance your website can still use MD5 hash. Such occasions might be:
- You migrated a WordPress website and user database from an old system
- You use old versions of WordPress plugins
- You are using an old version of WordPress.
Regardless of the occasion, to prevent your website from being easily hacked, follow our tips in the next sections.
How to Prevent WordPress MD5 Hash Decrypt Exploits on Your Website
There are many steps you can take to prevent WordPress MD5 hash decrypt exploits and make your website more secure and reliable. Here are some suggestions.
1. Update WordPress Core
A simple way of preventing MD5 decrypt exploits and improving your website’s security is by using a fresh copy of the latest WordPress version available. It is highly advisable to constantly check and install updates, as they provide you with one more layer of protection. Read how to update WordPress and take the first step in preventing MD4 hash exploits on your website. Also, when updating WordPress, don’t forget to back up your website as a protection from unforeseen events.
Read also: How to Restore Your WordPress Website From a Backup
2. Update WordPress Plugins
A second straightforward method of preventing MD5 hash exploits is by updating your installed plugins to the latest version available. Similar to WordPress core, plugins should be constantly updated to make sure they function properly and don’t create technical issues on your website. As a rule of thumb, always use plugins from reliable developers and always back up your website before installing and using plugins.
3. Rehash Old MD5 Passwords
Should you use an old version of WordPress, chances are that some stored passwords are still hashed with the MD5 hash. Luckily, WordPress can update the old passwords the next time a user logs in. To make it happen, you can create a simple plugin and activate it on the go.
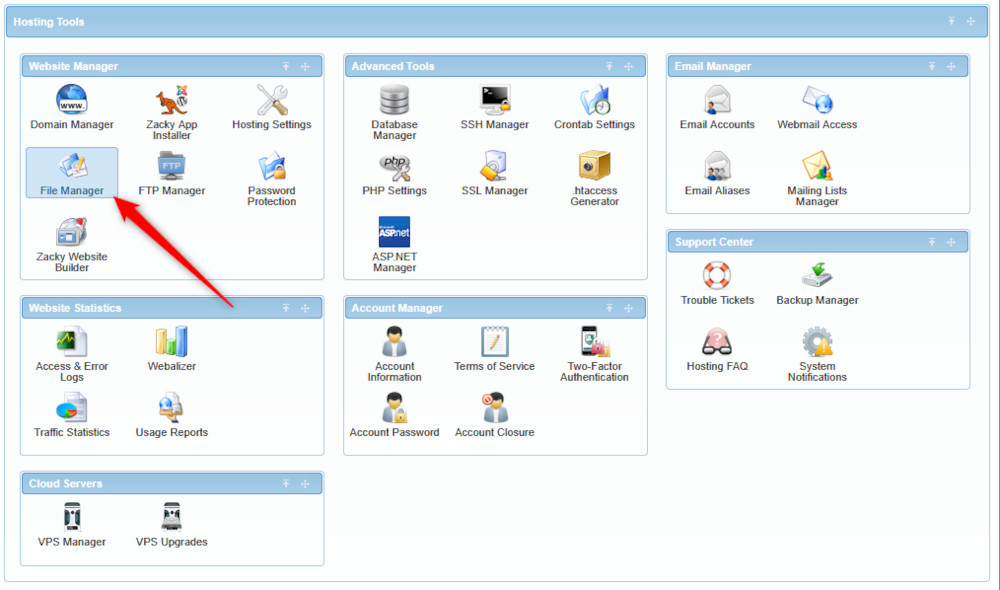
To start the process, log in to the AwradSpace hosting panel and head to File Manager:
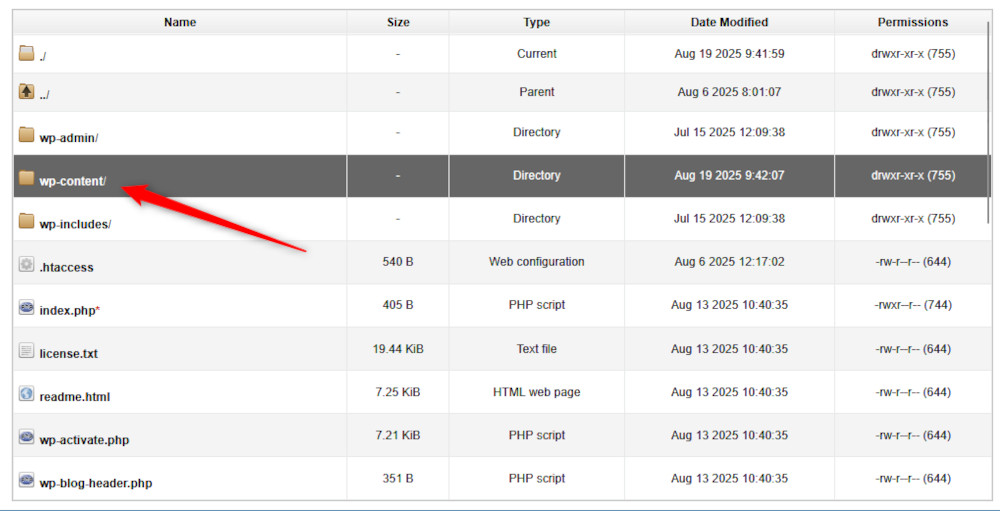
Then, open the root folder of your WordPress website and head to wp-content/:
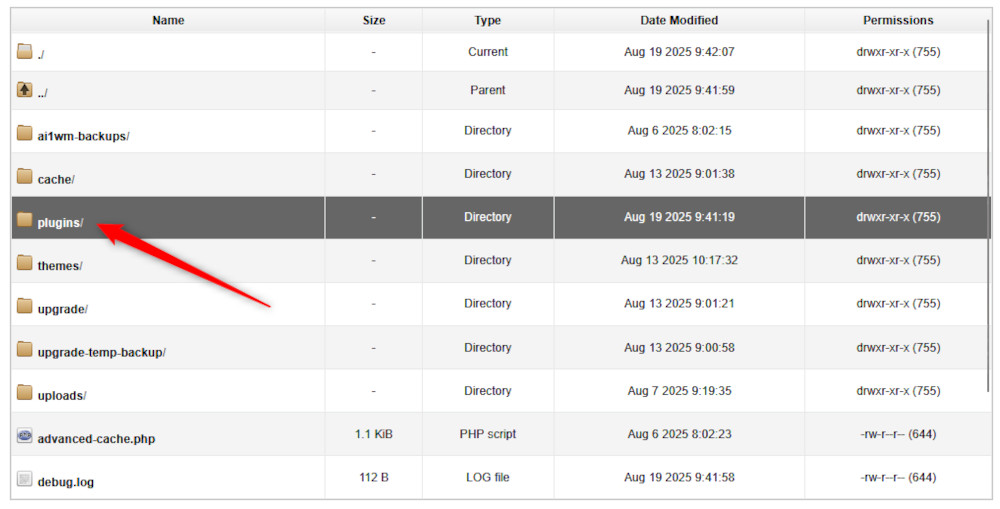
Then, open the plugins/ folder:
Inside, create a new folder by clicking the blue Create button at the top of the page:
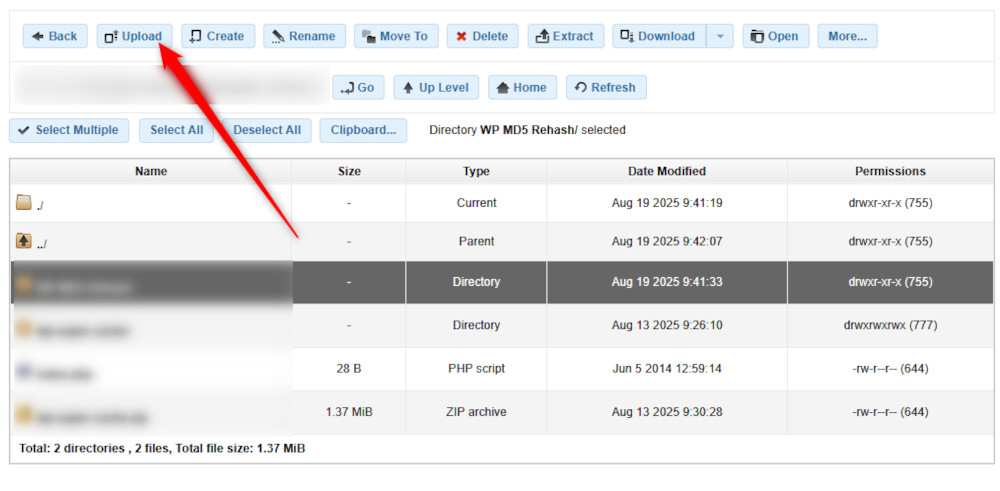
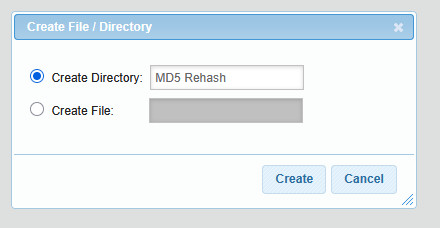
From the options, select Create Directory and name it as you wish, for example, MD5 Rehash:
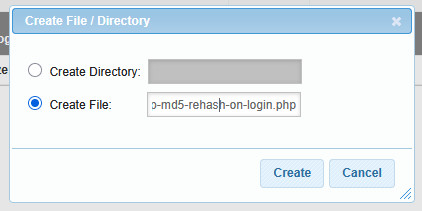
Then, open this older and inside, create a new file. To do so, click on the Create button at the top of the page and select the Create File options. Add a name to the file, and make sure to add a .PHP extension:
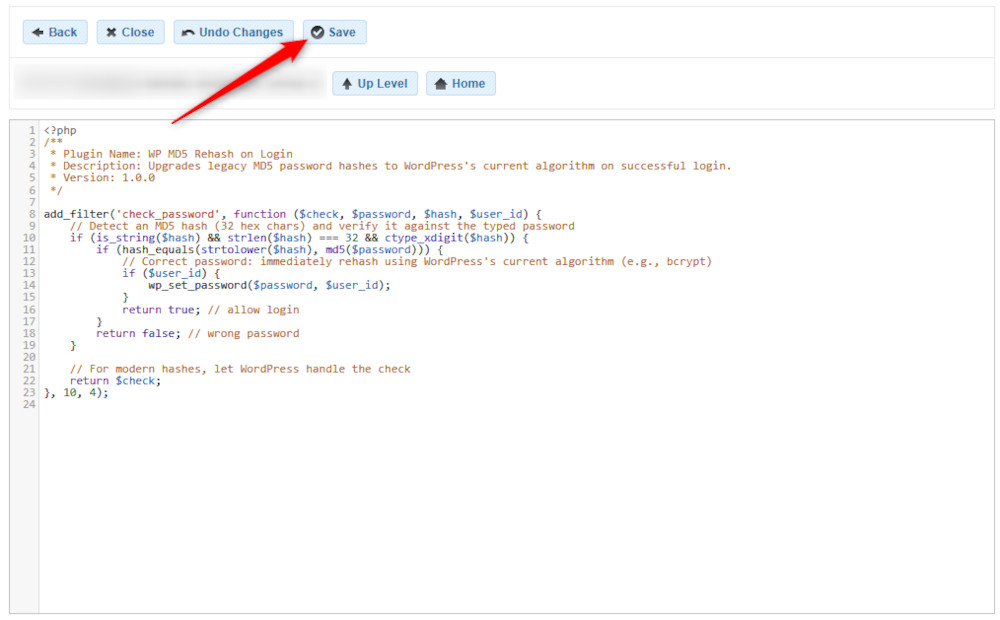
Then, open this newly created file and add this string of code inside:
<?php
/**
* Plugin Name: WP MD5 Rehash on Login
* Description: Upgrades legacy MD5 password hashes to WordPress’s current algorithm on successful login.
* Version: 1.0.0
*/
add_filter(‘check_password’, function ($check, $password, $hash, $user_id) {
// Detect an MD5 hash (32 hex chars) and verify it against the typed password
if (is_string($hash) && strlen($hash) === 32 && ctype_xdigit($hash)) {
if (hash_equals(strtolower($hash), md5($password))) {
// Correct password: immediately rehash using WordPress’s current algorithm (e.g., bcrypt)
if ($user_id) {
wp_set_password($password, $user_id);
}
return true; // allow login
}
return false; // wrong password
}
// For modern hashes, let WordPress handle the check
return $check;
}, 10, 4);
After you have inserted this string, click on the Save button, so AwardSpace applies your changes:
Now, you should log in to WordPress and activate the plugin. After you enter the admin dashboard, head to Plugins -> Installed Plugins:
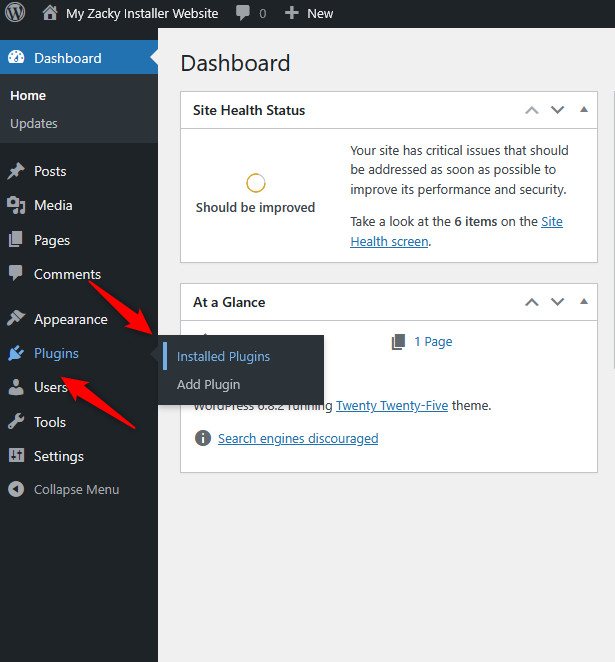
Then, click on Activate, so you engage the plugin you just created:
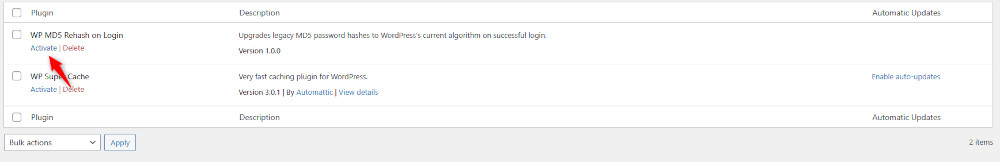
Now that the plugin is active, this is going to happen next time a user logs in to WordPress:
- A user will log in, and WordPress will automatically check their password.
- Should the stored password be hashed with MD5, the filter you created will activate.
- WordPress will instantly update the password database to a contemporary safety system.
4. (BONUS) Update Salts and Keys
Salts and keys are long random strings of symbols in WordPress that protect WordPress users from stolen data and cookies. Should these strings be old, weak, stolen, or exposed in any other way, attackers can reuse stolen cookies to enter your website. Although not directly tied to MD5 hashing, updating salts and keys can add one more layer of protection for your WordPress website.
The first step of the process is to go to the File Manager via the AwardSpace hosting panel (as shown above) and then head to the root directory of your WordPress website. There, locate a file named wp-config.php and open it:
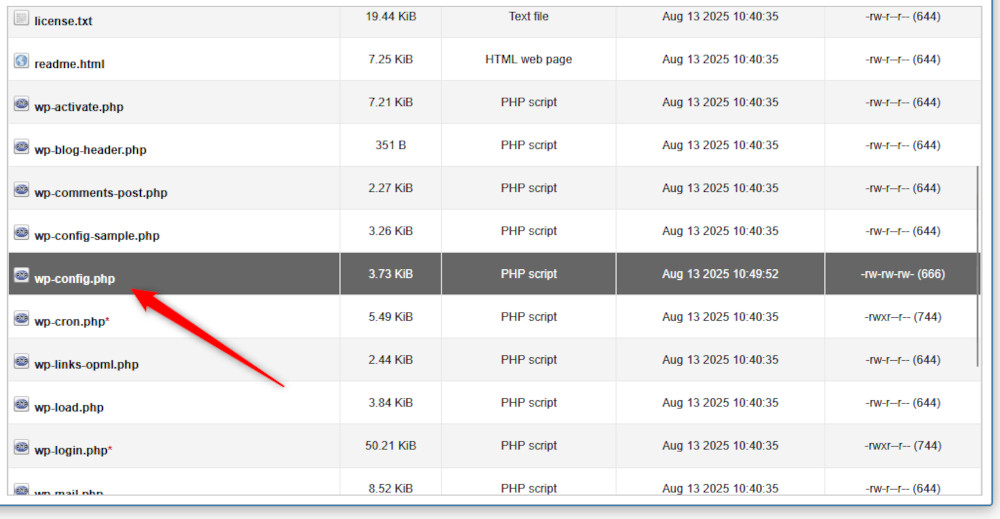
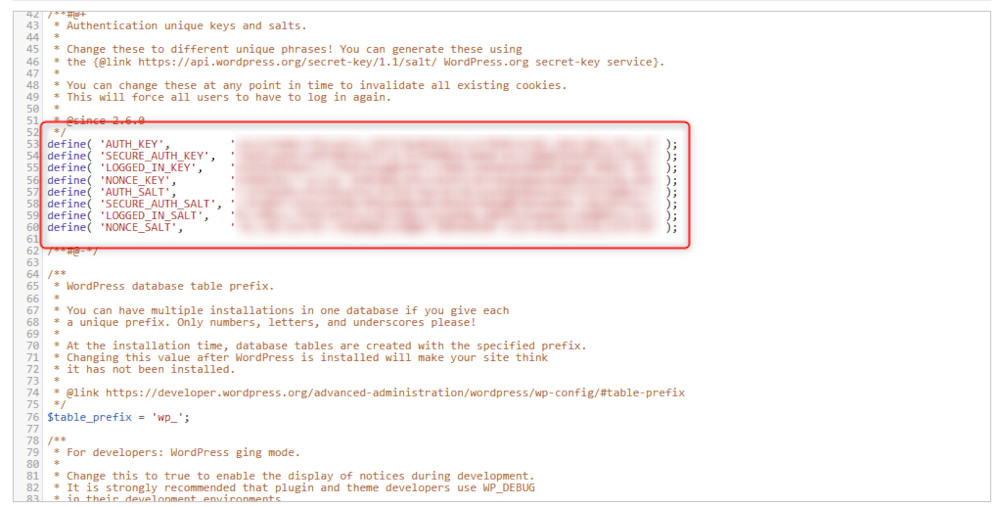
Then, within this file, locate these lines:
define(‘AUTH_KEY’, ‘…’);
define(‘SECURE_AUTH_KEY’, ‘…’);
define(‘LOGGED_IN_KEY’, ‘…’);
define(‘NONCE_KEY’, ‘…’);
define(‘AUTH_SALT’, ‘…’);
define(‘SECURE_AUTH_SALT’, ‘…’);
define(‘LOGGED_IN_SALT’, ‘…’);
define(‘NONCE_SALT’, ‘…’);
Within the file, they look like this:
Now, you need to replace these with new strings. To do so, open the official WordPress Salt Generator. It will generate new random strings. Once you see these, copy and replace the old string with the new ones. Don’t touch anything else within the file!
Once you have replaced the strings, click on Save, so the changes are applied:

Conclusion – How to Prevent WordPress MD5 Hash Decrypt Exploits
MD5 was a thing of beauty back in the day, but today it is obsolete and makes your website vulnerable. To prevent vulnerability issues tied to remaining MD5 hashes, you should always update WordPress and plugins, and upgrade old MD5 passwords to new versions, so you make sure your website is safe and sound.